Category: Privacy Guides

In today’s digital world, privacy guides are essential tools that help you understand how to safeguard your personal information online. These guides cover everything from managing social media settings to using strong passwords and recognizing phishing attempts. They explain complex topics in simple terms, making it easier for everyone to stay safe.
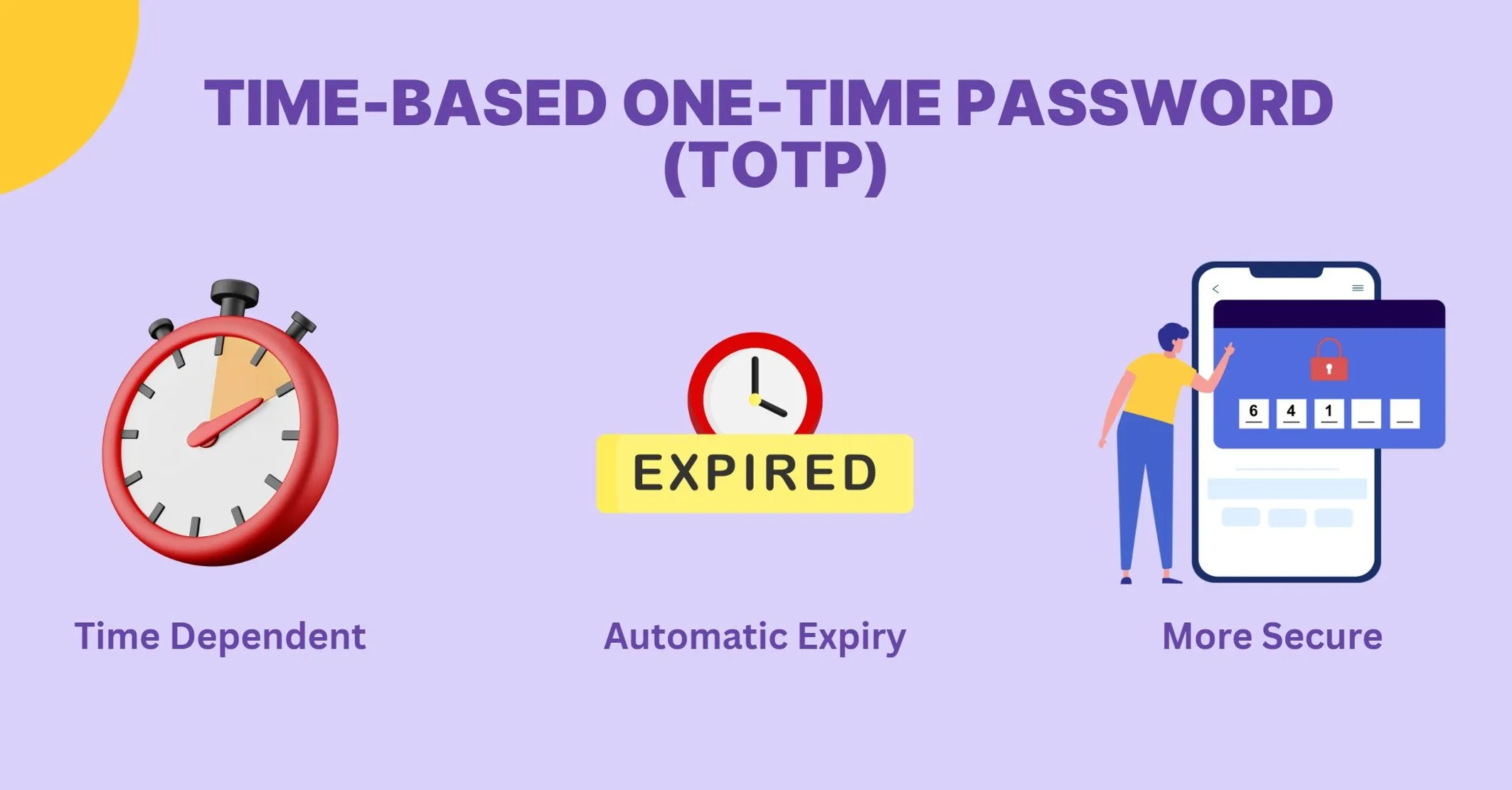
A good privacy guide will walk you through practical steps, such as adjusting app permissions, enabling two-factor authentication, and clearing browsing history. Many also highlight common pitfalls, like oversharing on public profiles or blindly accepting cookies without reading policies.
Using privacy guides regularly can empower you to take control of your data, reduce online risks, and enjoy a safer digital experience. Whether you’re a tech novice or a seasoned internet user, these guides offer valuable advice that fits seamlessly into your everyday routine.